Motivation
This is the second article in the “Private Virtual Network VPN” series. In the first article, I introduced how to set up a Shadowsocks service on a cloud server to achieve secure internet access from abroad based on my own needs. This article will cover the basic concepts of VPNs and focus on how to use Tailscale to set up a private virtual network. The other articles in this series are as follows:
VPN Basic Concepts
When we talk about VPNs, we often think of accessing websites that are blocked by firewalls or accessing corporate intranets and campus networks. In fact, the use cases for VPNs go far beyond that. VPNs can help us establish a secure tunnel between different networks, enabling data encryption and privacy protection. They can be used for remote work, cross-border access, data transmission, and more.
For example, I regularly use multiple computers, including those at home, in the office, and on cloud servers. These computers are located in different regions and networks; for instance, the office computer is on the company’s local area network, while the cloud servers are on Alibaba Cloud and Huawei Cloud, and they may even be distributed across different countries and regions. To facilitate file transfer and remote access between these computers, VPNs come into play.
Use Cases
For me, the main use cases for VPNs are as follows:
- SSH Remote Login: Although it is also possible to log in via SSH using a public IP, the public IP is unstable. Of course, dynamic domain name resolution can be used, but dynamic domain name resolution updates are often not timely, and dynamic IP resolution services may also go down. After using a VPN, all computers are on the same virtual network and can log in via SSH using the internal IP.
- Remote Desktop: Similarly, after using a VPN, all computers are on the same virtual network and can log in via remote desktop using the internal IP.
- File Transfer: After using a VPN, all computers are on the same virtual network and can transfer files using the internal IP.
- Accessing Network Services on Other Computers: This can be divided into several scenarios:
- For example, when I am abroad, NetEase Cloud Music will determine that I am abroad based on my IP address, and thus I cannot listen to certain region-restricted music. After using a VPN, I can proxy the requests from NetEase Cloud Music to a computer located in China, pretending to be in China, and I can listen to music normally.
- For example, when I am in China, I cannot access websites such as Google and GitHub. After using a VPN, I can proxy the requests from Google and GitHub to a computer located abroad, pretending to be abroad, and I can access them normally.
VPN Principles
The principle of VPN is to establish a virtual private network over the public internet, connecting different networks together. VPN uses encryption technology to encrypt data, ensuring the security and privacy of the data. The working principle of VPN can be divided into the following steps:
- Establishing Connection: The client establishes a connection with the VPN server through VPN client software. This process is usually encrypted using protocols such as SSL/TLS.
- Authentication: The client sends authentication information, such as a username and password, to the VPN server. The VPN server verifies the identity to ensure the client is a legitimate user.
- Establishing Tunnel: After successful authentication, an encrypted tunnel is established between the VPN server and the client. This tunnel can be based on protocols such as IPsec, L2TP, or PPTP.
- Data Transmission: Data between the client and the VPN server is transmitted through the encrypted tunnel. The data is encrypted during transmission to ensure its security and privacy.
- Disconnecting: When the client no longer needs to use the VPN, it can disconnect from the VPN server through the VPN client software. At this point, the VPN tunnel will also be closed.
Tailscale
Tailscale Overview
Tailscale is a VPN solution based on WireGuard that helps us quickly set up a private virtual network. Tailscale is characterized by its ease of use, cross-platform support, and automatic NAT traversal. It can be used on multiple platforms, including Windows, macOS, Linux, iOS, and Android.
WireGuard is a modern VPN protocol that uses the latest encryption technology, offering high performance and low latency. The design goals of WireGuard are simplicity, security, and efficiency. Its codebase is very small, consisting of only a few thousand lines of code, making it much smaller than other VPN protocols (such as OpenVPN, IPsec, etc.). This makes WireGuard easier to audit and maintain.
Tailscale Working Principle
Tailscale’s working principle is to manage all clients through a centralized control server. Each client, when connecting to Tailscale, registers its IP address and public key with the control server. The control server distributes this information to other clients, enabling peer-to-peer connections.
Tailscale uses the WireGuard protocol to establish encrypted tunnels. Each client has a WireGuard private key and public key. Through the control server, clients can obtain the public keys of other clients, allowing them to establish peer-to-peer connections.
Tailscale also supports automatic NAT traversal and firewall penetration, making it usable in various network environments. It employs technologies such as STUN and TURN to achieve NAT traversal.
Tailscale also supports access control and authentication. It can integrate with identity providers such as Google, Microsoft, and GitHub to achieve single sign-on (SSO). This allows Tailscale to seamlessly integrate with existing identity management systems.
Tailscale Advantages and Disadvantages
Advantages of Tailscale:
- Easy to use: Tailscale’s installation and configuration are very simple, allowing you to set up a private virtual network in just a few minutes.
- Cross-platform support: Tailscale supports multiple platforms, including Windows, macOS, Linux, iOS, and Android.
- Automatic NAT traversal: Tailscale can automatically traverse NAT and firewalls without manual port forwarding configuration.
- High performance: Tailscale uses the WireGuard protocol, offering high performance and low latency.
- Security: Tailscale employs the latest encryption technologies to ensure data security and privacy.
- Access control: Tailscale supports access control and authentication, allowing integration with existing identity management systems.
- Low cost: Tailscale’s free version supports up to 20 devices, making it suitable for individuals and small teams.
- Open source: The core components of Tailscale are open source and can be found on GitHub.
- Community support: Tailscale has an active community that can provide technical support and assistance.
- Comprehensive documentation: Tailscale’s documentation is very detailed, providing a wealth of use cases and tutorials.
- Monitoring and logging: Tailscale provides monitoring and logging features to help troubleshoot issues and optimize performance.
Disadvantages of Tailscale:
- Centralization: Tailscale uses a centralized control server to manage clients, which may lead to single points of failure and privacy concerns.
- Network dependency: Tailscale relies on network connectivity, and if the network is unstable, it may affect VPN performance.
Tailscale Usage Methods
Tailscale has two usage methods: one is to use Tailscale’s official control server, and the other is to self-host a control server. For most users, using the official control server is sufficient. However, if you have higher requirements for privacy and security, or if you have special needs that require greater flexibility, you will need to self-host a control server.
Here, we will briefly introduce the first usage method, which is to use Tailscale’s official control server. The second usage method, self-hosting a control server, will not be covered in detail here, but a separate article will be written to introduce it.
Register an account: Visit the Tailscale website to register an account. You can log in using your Google, Microsoft, GitHub, or other accounts.
Install Tailscale: Install Tailscale on the devices that need to connect. You can use the following command to install:
Windows: Download the Windows installer and install it.
macOS: Download the macOS installer and install it.
Linux: Use the following command to install:
1curl -fsSL https://tailscale.com/install.sh | shiOS and Android: Search for “Tailscale” in the App Store or Google Play and install it.
Log in: After installation, Tailscale will open a browser window prompting you to log in using your registered account or a third-party account like Google, Microsoft, or GitHub.
Connect: Once logged in, Tailscale will automatically assign an IP address to the device. You can view the list of devices and their IP addresses in the Tailscale app:
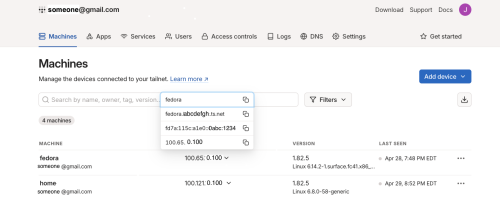
Access other devices: Devices on the same Tailscale network can be accessed directly via their IP addresses. For example, you can use the ssh command to log in to the Fedora device mentioned above:
1ssh [email protected]You can also access other devices via the DNS names provided by Tailscale, for example:
1ssh [email protected]Set up access control: You can set up access control rules in the Tailscale app, such as restricting access between certain devices.
Disconnect: When you no longer need to use Tailscale, you can disconnect in the Tailscale app.